This is step by step guide to configure App Registration on Azure Active Directory (AzureAD). This guide includes three ways to create App Registration using Azure Portal, PowerShell and AzureCLI.
Azure Portal
Within Azure AD portal you will find the App registrations pane that provide the capability to produce registrations for applications and assign permissions accordingly. Microsoft provides a robust identity platform – Azure active directory (AzureAD), but to permit authentication and authorization applications need to be recorded. When you provision an application, you create a trust relationship between the defined application and the Microsoft identity platform.
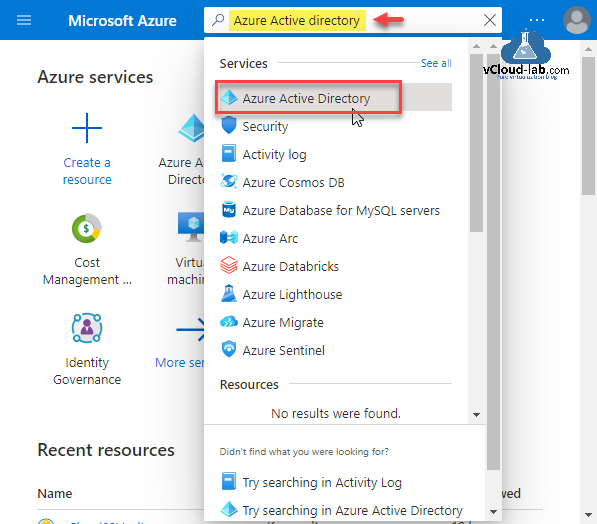
Go to the search bar on Microsoft Azure Portal and search Azure Active Directory and click on it.
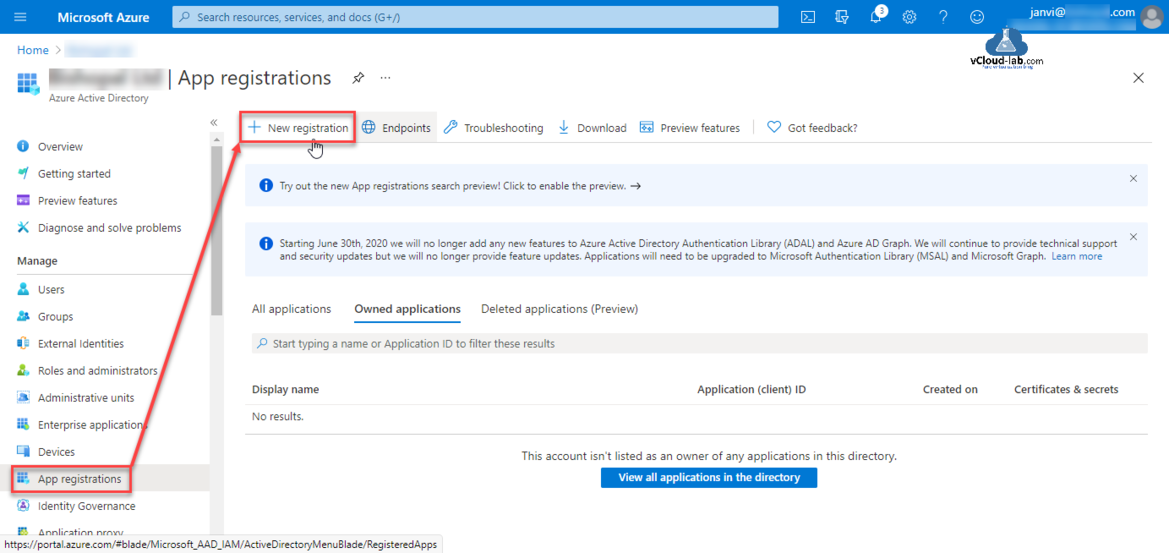
Click App Registrations then press + New registration.
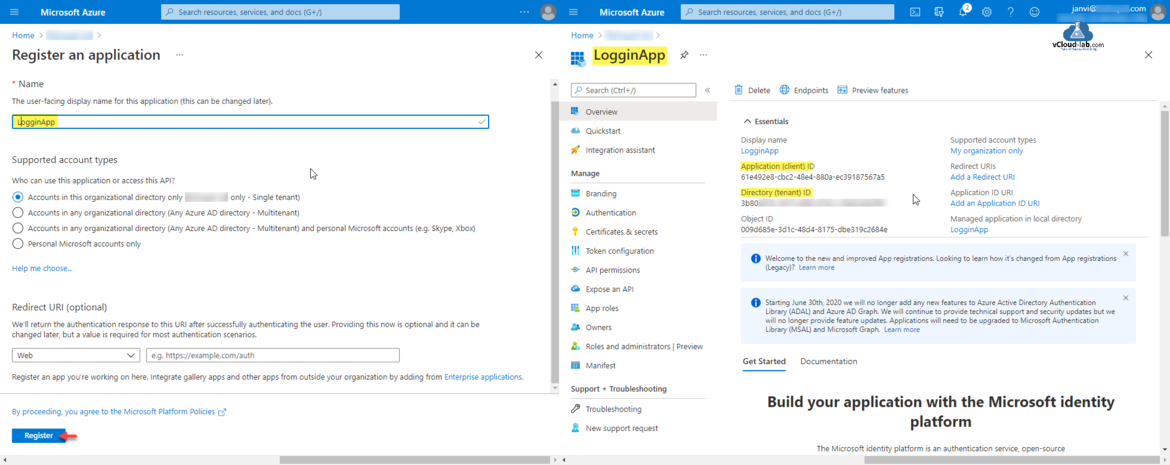
I am keeping all the selection option default. In the Register an application type the name the user-facing display name for the application (this can be changed later). Next option is who can use this application or access this API? Selected supported account types is selected is Accounts in this organization directory only - Single tenant. Click Register button.
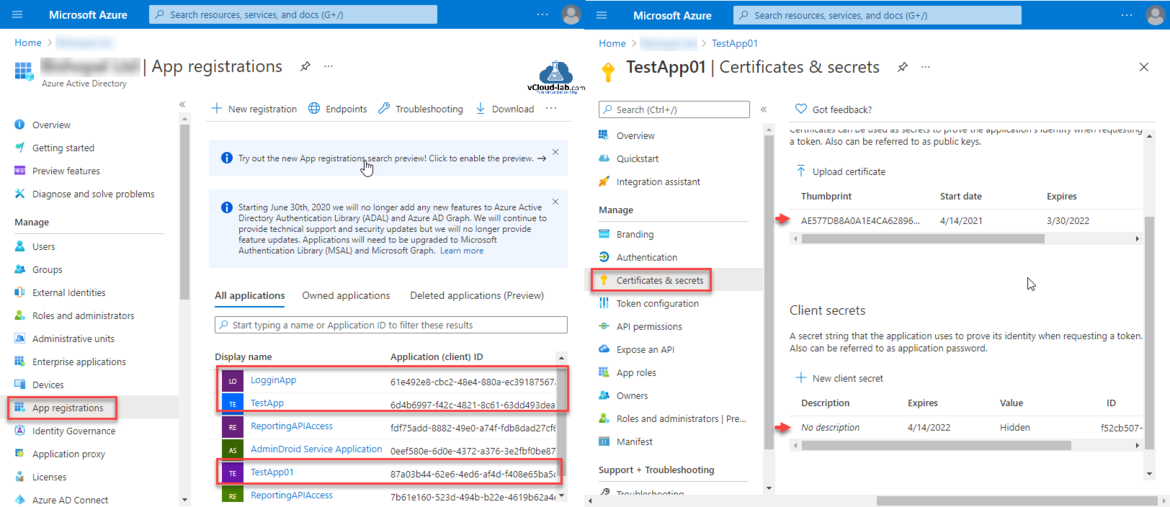
Once Application is registered Note down the Application (client ID) and Object Id. It can be use them later as (Client ID) username for authentication.
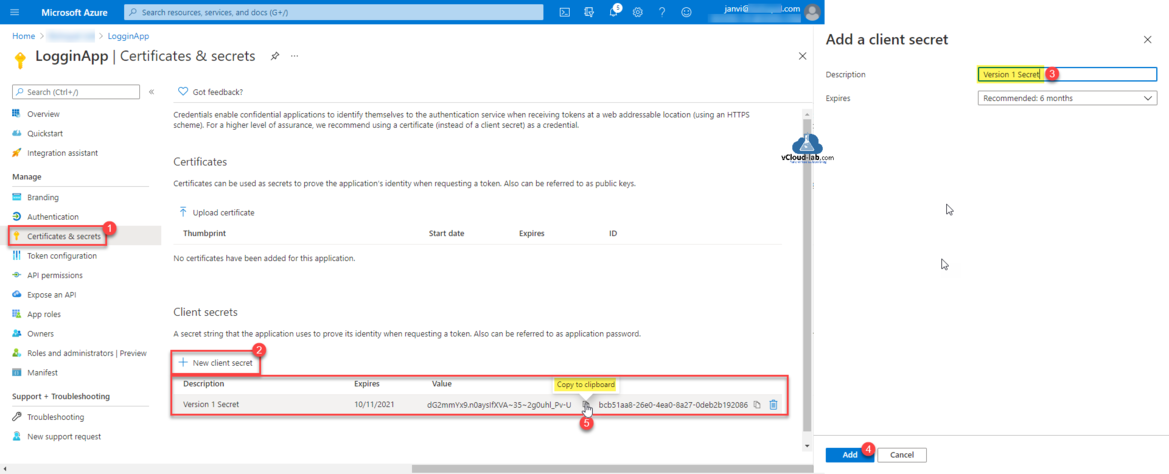
Add a App client Secret going to Certificates & secrets. Click New client secret. Type description and expiry time for secret and click Add. Once secret is generated copy password value to clipboard and keep it safe saved so it can be used until it expires as client secret (password).
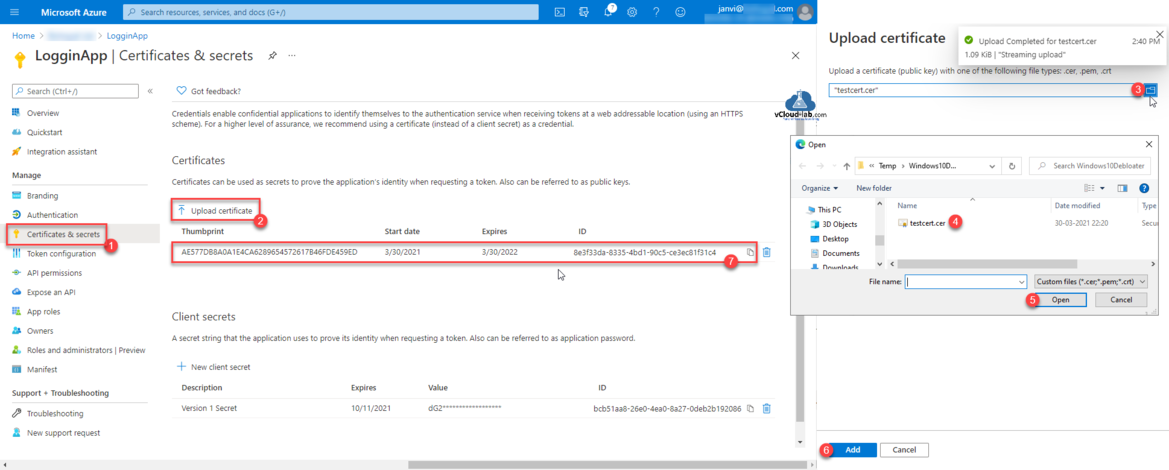
Next procedure is to Upload certificate, Select certificate file and upload it. I will use it in one of the next article.
PowerShell Az module
In this PowerShell az module, I can create only register AAD application. To configure certificate and secret on AAD app use seperate AzureAD Powershell module.
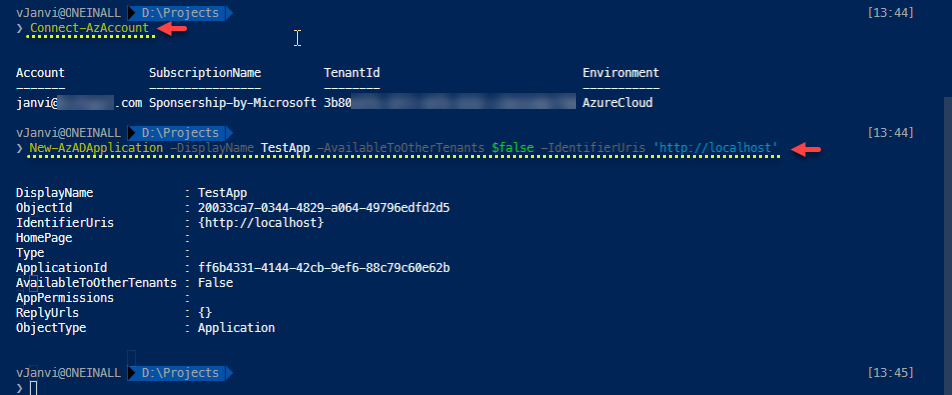
❯ Connect-AzAccount ❯ New-AzADApplication -DisplayName TestApp -AvailableToOtherTenants $false -IdentifierUris 'http://localhost'
PowerShell AzureAD module
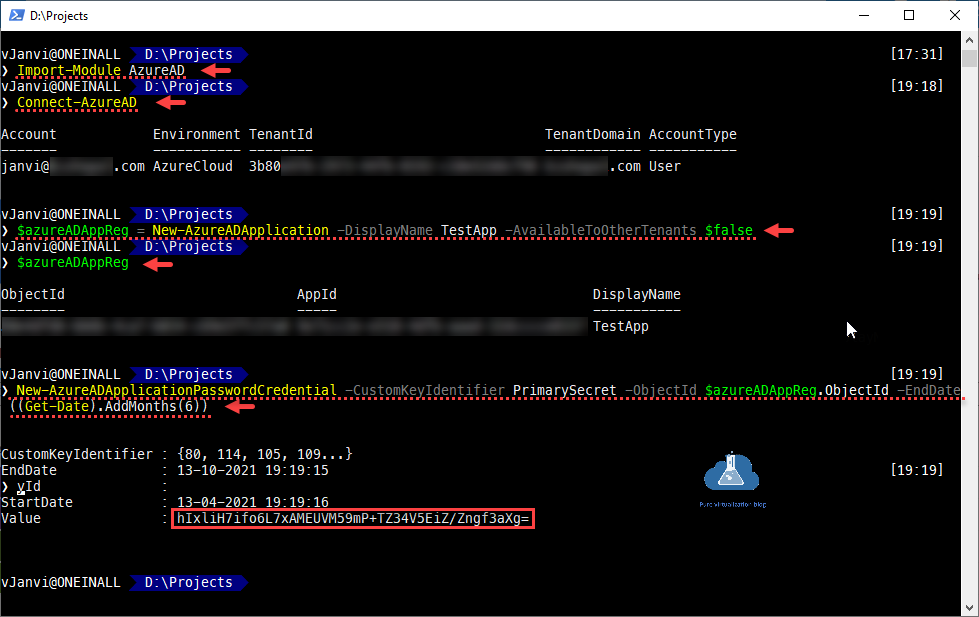
Default az module doesn't have much cmdlets to manage AAD App registrations. Instead If I use AzureAD Powershell module I have more options to manage AAD applications. Here I have created Secret for AD application once it is created. Note down the secret Value.
❯ Import-Module AzureAD ❯ Connect-AzureAD ❯ $azureADAppReg = New-AzureADApplication -DisplayName TestApp -AvailableToOtherTenants $false ❯ $azureADAppReg ❯ New-AzureADApplicationPasswordCredential -CustomKeyIdentifier PrimarySecret -ObjectId $azureADAppReg.ObjectId -EndDate ((Get-Date).AddMonths(6))
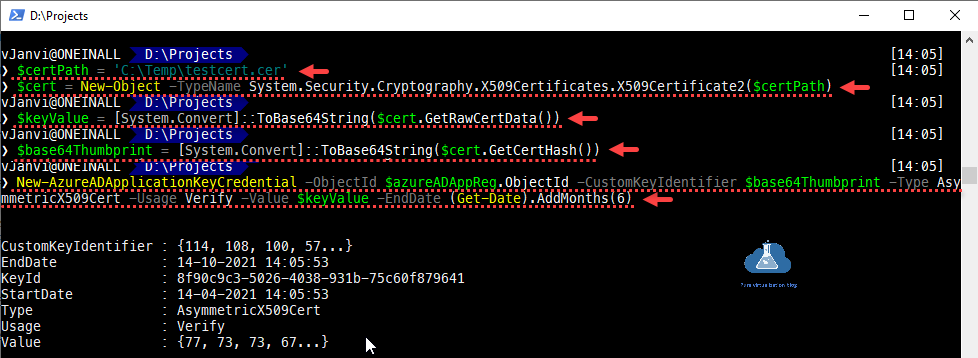
Below PowerShell cmdlet helps to upload certificate on the AAD Apps Registrations.
❯ $certPath = 'C:\Temp\testcert.cer' ❯ $cert = New-Object -TypeName System.Security.Cryptography.X509Certificates.X509Certificate2($certPath) ❯ $keyValue = [System.Convert]::ToBase64String($cert.GetRawCertData()) ❯ $base64Thumbprint = [System.Convert]::ToBase64String($cert.GetCertHash()) ❯ New-AzureADApplicationKeyCredential -ObjectId $azureADAppReg.ObjectId -CustomKeyIdentifier $base64Thumbprint -Type AsymmetricX509Cert -Usage Verify -Value $keyValue -EndDate (Get-Date).AddMonths(6)
AzureCLI
Using AzureCLI commands to register application under Azure AD is very easy.
Part 1: Working With Azure Key Vault Using Azure PowerShell and AzureCLI
Part 2: Create a Virtual machine on Microsoft Azure
Part 3: Use a Azure VM system assigned managed identity to access Azure Key Vault
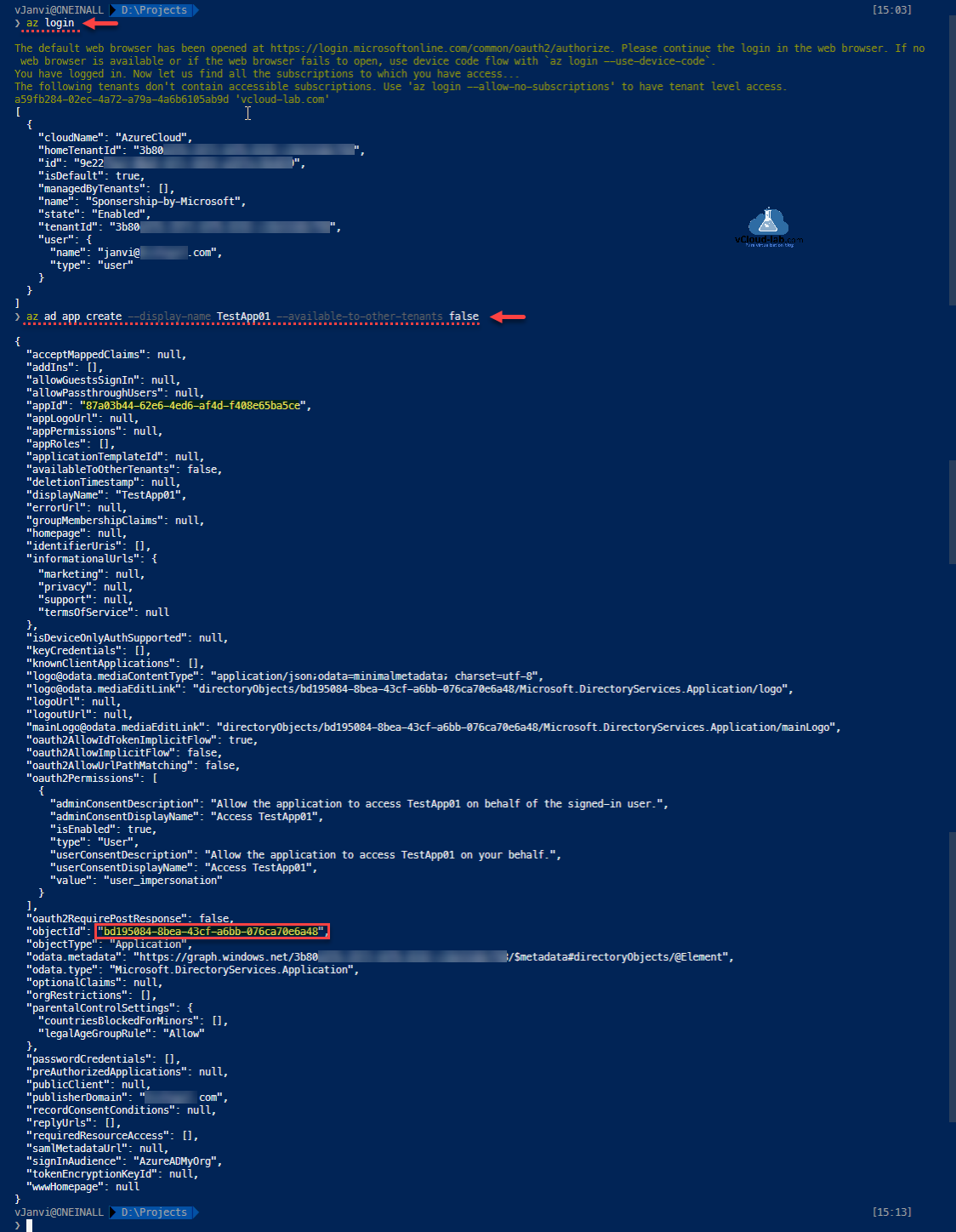
❯ az login The default web browser has been opened at https://login.microsoftonline.com/common/oauth2/authorize. Please continue the login in the web browser. If no web browser is available or if the web browser fails to open, use device code flow with `az login --use-device-code`. You have logged in. Now let us find all the subscriptions to which you have access... The following tenants don't contain accessible subscriptions. Use 'az login --allow-no-subscriptions' to have tenant level access. a59fb284-02ec-4a72-a79a-4a6b6105ab9d 'vcloud-lab.com' [ { "cloudName": "AzureCloud", "homeTenantId": "3b80xxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx", "id": "9e22xxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx", "isDefault": true, "managedByTenants": [], "name": "Sponsership-by-Microsoft", "state": "Enabled", "tenantId": "3b80xxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx", "user": { "name": "janvi@vcloud-lab.com", "type": "user" } } ] ❯ az ad app create --display-name TestApp01 --available-to-other-tenants false { "acceptMappedClaims": null, "addIns": [], "allowGuestsSignIn": null, "allowPassthroughUsers": null, "appId": "87a03b44-62e6-4ed6-af4d-f408e65ba5ce", "appLogoUrl": null, "appPermissions": null, "appRoles": [], "applicationTemplateId": null, "availableToOtherTenants": false, "deletionTimestamp": null, "displayName": "TestApp01", "errorUrl": null, "groupMembershipClaims": null, "homepage": null, "identifierUris": [], "informationalUrls": { "marketing": null, "privacy": null, "support": null, "termsOfService": null }, "isDeviceOnlyAuthSupported": null, "keyCredentials": [], "knownClientApplications": [], "logo@odata.mediaContentType": "application/json;odata=minimalmetadata; charset=utf-8", "logo@odata.mediaEditLink": "directoryObjects/bd195084-8bea-43cf-a6bb-076ca70e6a48/Microsoft.DirectoryServices.Application/logo", "logoUrl": null, "logoutUrl": null, "mainLogo@odata.mediaEditLink": "directoryObjects/bd195084-8bea-43cf-a6bb-076ca70e6a48/Microsoft.DirectoryServices.Application/mainLogo", "oauth2AllowIdTokenImplicitFlow": true, "oauth2AllowImplicitFlow": false, "oauth2AllowUrlPathMatching": false, "oauth2Permissions": [ { "adminConsentDescription": "Allow the application to access TestApp01 on behalf of the signed-in user.", "adminConsentDisplayName": "Access TestApp01", "isEnabled": true, "type": "User", "userConsentDescription": "Allow the application to access TestApp01 on your behalf.", "userConsentDisplayName": "Access TestApp01", "value": "user_impersonation" } ], "oauth2RequirePostResponse": false, "objectId": "bd195084-8bea-43cf-a6bb-076ca70e6a48", "objectType": "Application", "odata.metadata": "https://graph.windows.net/3b80e97b-2973-44fb-8192-c18e52ddcf98/$metadata#directoryObjects/@Element", "odata.type": "Microsoft.DirectoryServices.Application", "optionalClaims": null, "orgRestrictions": [], "parentalControlSettings": { "countriesBlockedForMinors": [], "legalAgeGroupRule": "Allow" }, "passwordCredentials": [], "preAuthorizedApplications": null, "publicClient": null, "publisherDomain": "vcloud-lab.com", "recordConsentConditions": null, "replyUrls": [], "requiredResourceAccess": [], "samlMetadataUrl": null, "signInAudience": "AzureADMyOrg", "tokenEncryptionKeyId": null, "wwwHomepage": null }
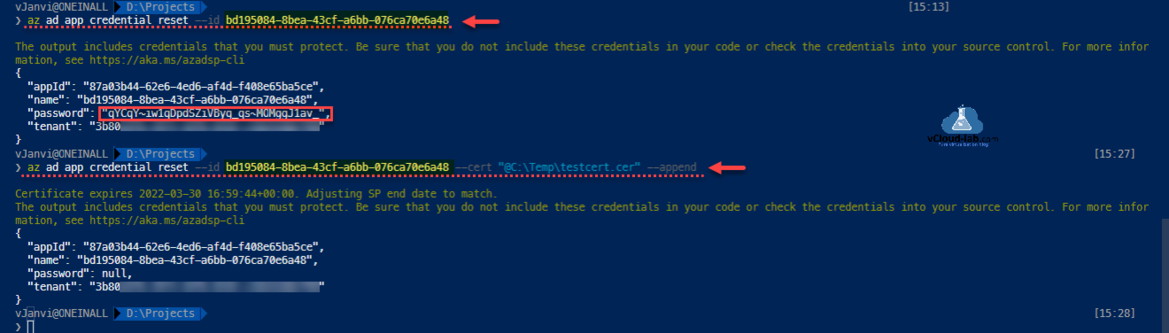
Once App registraions are created Secret password generation and uploading certificate is even easier with Azure CLI commands, All can be done with one-liner commands.
❯ az ad app credential reset --id bd195084-8bea-43cf-a6bb-076ca70e6a48 --credential-description TestSecret ❯ az ad app credential reset --id bd195084-8bea-43cf-a6bb-076ca70e6a48 --cert "@C:\Temp\testcert.cer" --append
Download this script here or it is also available on github.com.
Useful Articles
Use Key Vault secret identifier url to get the secret value using Powershell
Create key vault and secrets with access policies in Microsoft Azure
Working With Azure Key Vault Using Azure PowerShell and AzureCLI
Creating a new user in Azure AD using oneliner PowerShell and Azure CLI
Create and manage Azure budgets
Connect-AzAccount The 'Connect-AzAccount' command was found in the module 'Az.Accounts', but the module could not be loaded
Microsoft Azure Rest API using PowerShell
Microsoft Azure Rest API using PowerShell Part 2