This guide is not specific to configuration but it also shows how I troubleshooted CA signed certificate issue while configuring WinRM listener. This is a third part of PowerShell remoting over HTTPS using self-signed SSL certificate, For security best practices instead of going with Self signed certificate I am using CA signed certificate. First step I need is CSR file, I have used below two openssl commands to generate CSR file as shown on article before Configure Powershell WinRM to use OpenSSL generated Self-Signed certificate.
openssl genrsa -out Priv.key 2048
openssl req -new -key Priv.key -out Request.csr -config psremote002.cnf
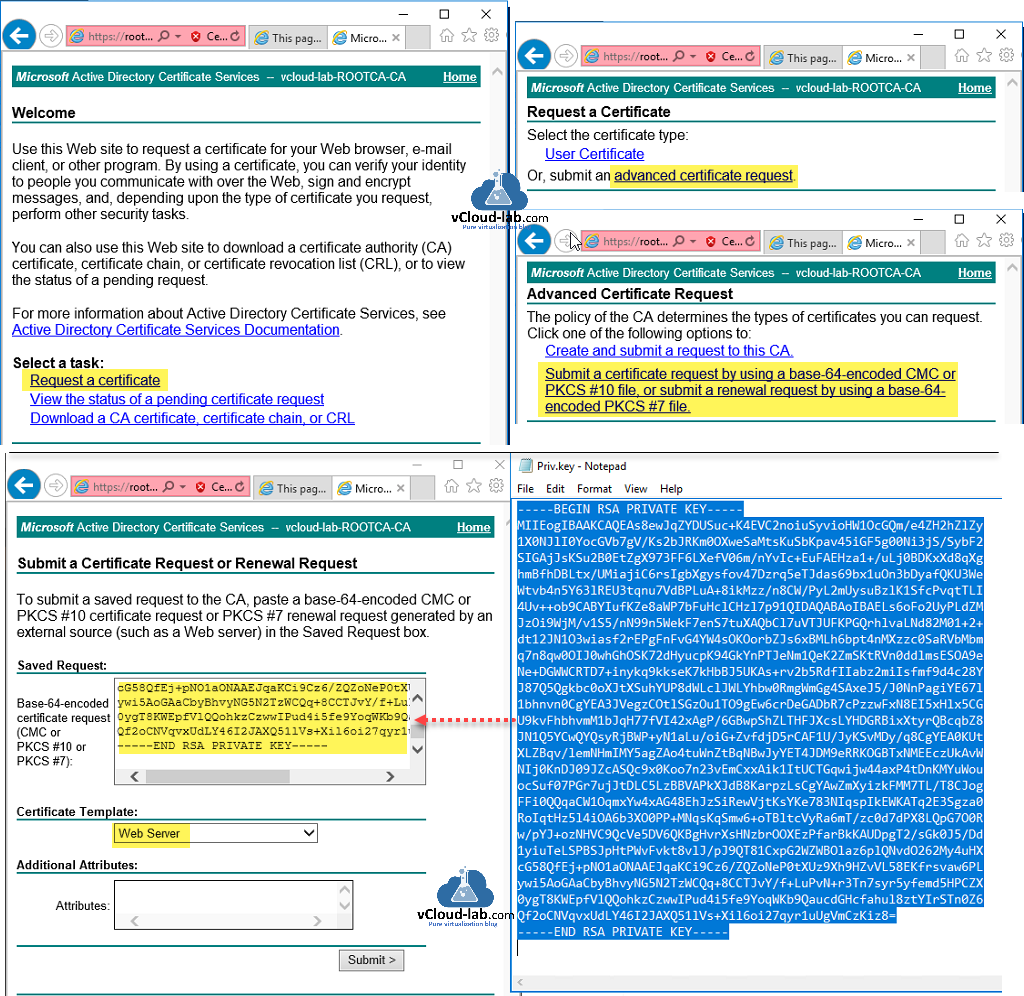
Once you have a CSR ready, open your certificate authority url website, choose Request a certificate then press on Submit an advanced certificate request link, here click Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file. On the next page open Request.CSR in notepad select all and copy the contents, paste to Saved request textbox, last choose Web server as certificate template. Submit to download CA generated certificate.
Series
POWERSHELL PS REMOTING BETWEEN STANDALONE WORKGROUP COMPUTERS
PowerShell remoting over HTTPS using self-signed SSL certificate
Configure Powershell WinRM to use OpenSSL generated Self-Signed certificate
Powershell WinRM HTTPs CA signed certificate configuration
Powershell Generate Self-signed certificate with Self-Signed Root CA Signer
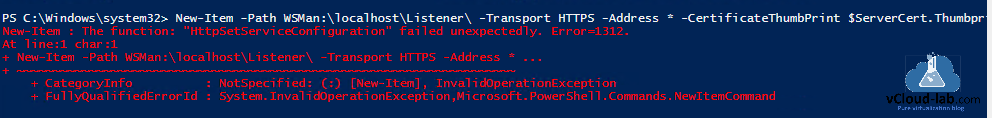
I downloaded certificate and uploaded to local machines \ personal certificate store but while configuring certificate thumbprint as a new HTTPS listener for WinRM, I was keep receiving below error.
New-Item : The function: "HttpSetServiceConfiguration" failed unexpectedly. Error=1312.
At line:1 char:1
+ New-Item -Path WSMan:\localhost\Listener\ -Transport HTTPS -Address * ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [New-Item], InvalidOperationException
+ FullyQualifiedErrorId : System.InvalidOperationException,Microsoft.PowerShell.Commands.NewItemCommand
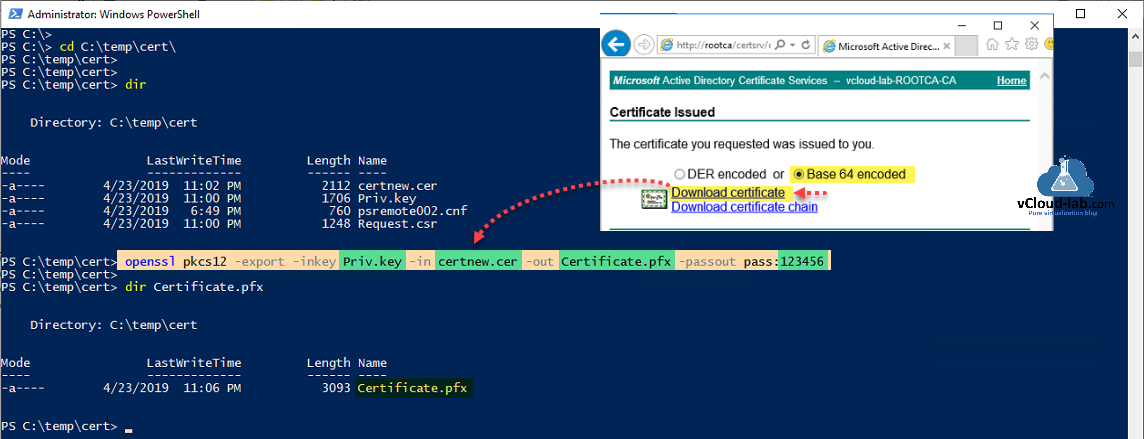
To dig down more I generated and downloaded certificate multiple times, but I was still receiving errors. After going through my earlier articles on same topics I found when CA generates a certificate, it doesn't have key in it, Before importing it to local certificate store, you need to create PFX file using private key and certnew.cer using openssl, then upload to cert store. (Personal Information Exchange Format (PFX) enables transfer of certificates and their private keys from one computer to another or to removable media.)
openssl pkcs12 -export -inkey Priv.key -in certnew.cer -out certificate.pfx -passout pass:123456
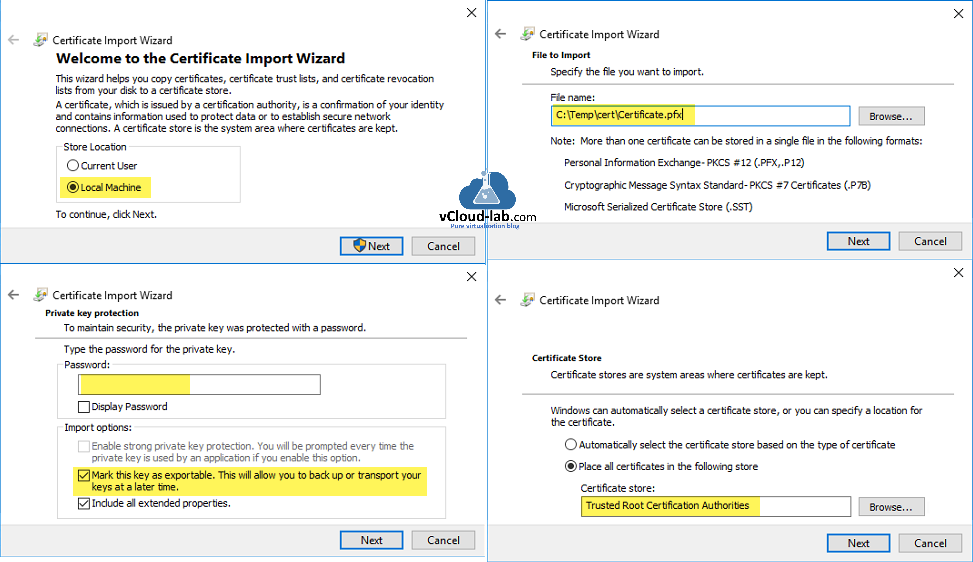
To upload the PFX file to local machine \ personal \ ceritificate store just double click file, It launches Certificate Import Wizard, select Local Machine, File to import will show file name which you are uploading, Next use the password and select Mark this key exportable, This will allow you to backup or transport your keys at later time, in the last browse for Trusted Root certification authorities (it should be personal for better management, but I want to show what is difference between .cer and .pfx)
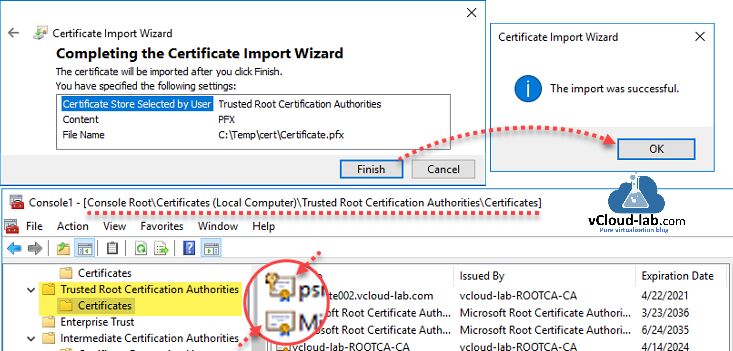
Review the setting on last page, click finish, the import should be successful. Open the certificate store and check the icons of existing certificates and new uploaded pfx, there is a key inbuilt in pfx certificate and listener require the key, Rest everything was working fine.
Use below command to check the connection.
Invoke-Command -ComputerName psremote002.vcloud-lab.com -ScriptBlock {hostname} -Credential (Get-Credential) -UseSSL -Port 5986
Useful Articles
POWERSHELL DSC XACTIVEDIRECTORY ERROR - A NETBIOS DOMAIN NAME MUST BE SPECIFIED
DSC (DESIRED STATE CONFIGURATION) : DEPLOYING ACTIVE DIRECTORY
THE POWERSHELL XACTIVEDIRECTORY PROVIDER DOES NOT EXIST AT THE POWERSHELL MODULE PATH NOR IS IT REGISTERED AS A WMI PROVIDER