This is step by step guide on basic vmware certificate chain installation in the infrastructure, all the steps performed on development infra, Back from my previous project, I installed new VMware vCenter appliance 6.7 recently and few of my esxi server were already installed with self signed certificates using Microsoft CA and openssl tool. But I wanted to streamline everything with automated fashion. VMCA to help here, VCSA 6.7 comes with component called VMCA (VMware certificate authority) inbuilt into PSC (Platform services controller).
Generate new self-signed certificates for ESXi using OpenSSL
Push SSL certificates to client computers using Group Policy
Replacing a default ESXi certificate with a CA-Signed certificate
Troubleshooting replacing a corrupted certificate on Esxi server
How to import default vCenter server appliance VMCA root certificate and refresh CA certificate on ESXi
How to replace default vCenter VMCA certificate with Microsoft CA signed certificate
Managing ESXi SSL certificate properties from vCenter server
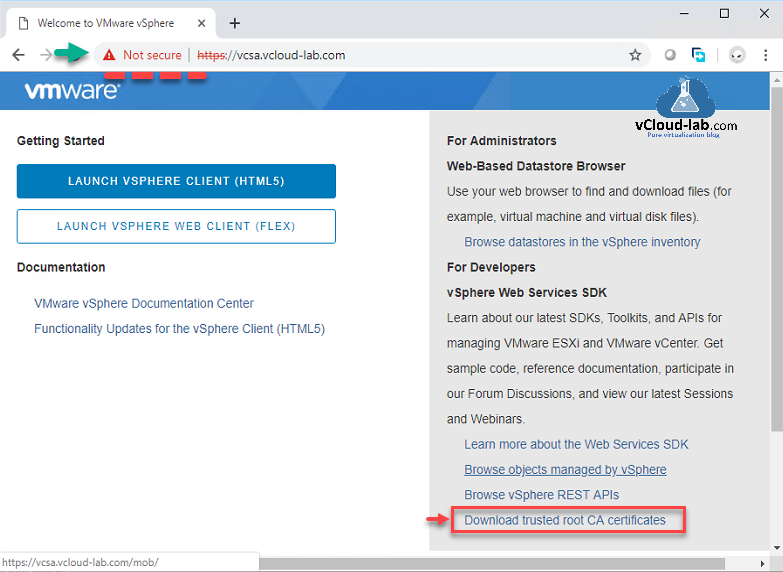
When you open VCSA web client url, by default it shows certificate error with not secure. If you open cert and read the properties it signed by unknown CA. To resolved this without any change, download VMCA root certificate chain from same webpage in the right bottom. Click on Download trusted root CA certificates.
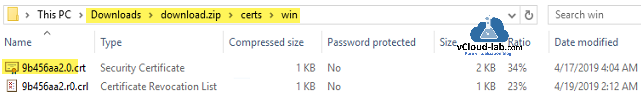
Inside the zip file, we will need CRT extension file located under path location certs\win. Extract it
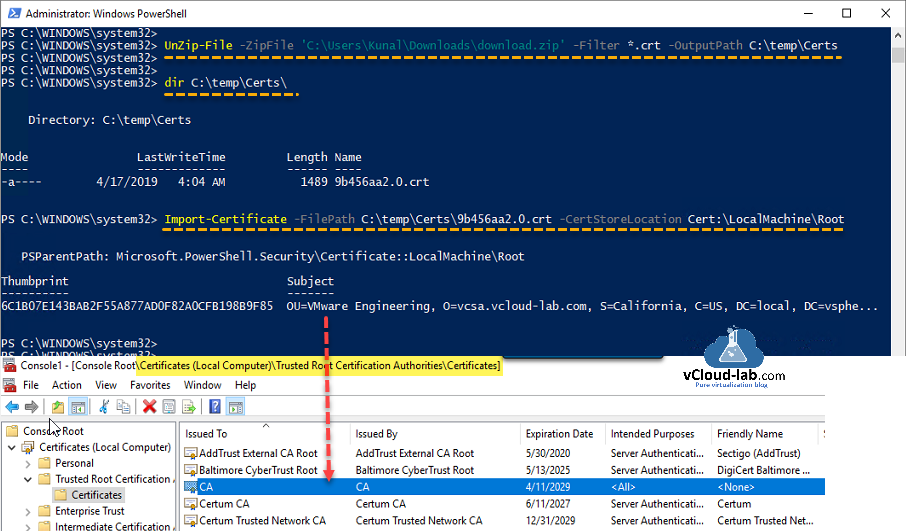
I am using below PowerShell script to extract required file.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 |
function UnZip-File { [CmdletBinding(SupportsShouldProcess=$True, ConfirmImpact='Medium', HelpURI='http://vcloud-lab.com', )] param ( [parameter(Position=1, Mandatory=$True, ValueFromPipelineByPropertyName=$true)] [alias('ZipPath')] [String]$ZipFile = "$env:USERPROFILE\Downloads\download.zip", [parameter(Position=2, Mandatory=$True, ValueFromPipelineByPropertyName=$true)] $Filter = '*.crt', [parameter(Position=3, ValueFromPipelineByPropertyName=$true)] $OutputPath = 'C:\Temp\Certs' ) $exists = Test-Path -Path $OutputPath if ($exists -eq $false) { $null = New-Item -Path $OutputPath -ItemType Directory -Force } Add-Type -AssemblyName System.IO.Compression.FileSystem $zip = [System.IO.Compression.ZipFile]::OpenRead($ZipFile) $foundFiles = $zip.Entries | Where-Object {$_.Fullname -like $Filter} foreach ($file in $foundFiles) { [System.IO.Compression.ZipFileExtensions]::ExtractToFile($file,"$OutputPath\$($file.Name)",$true) } $zip.Dispose() } |
Run above script once, after that execute below command to extract CRT file to Output path.
UnZip-File -ZipFile <Path\Zip> -Filter <*.ext> -OutputPath <Path>
Next command Imports certificate to local computer's Certificates MMC under location Trusted Root Certification Authorities\Certificates, Once import is successful you can verify it on the gui mmc. If you want to escape below step and want to push install chain certificate on your entire infrastructure use my previous article Push SSL certificates to client computers using Group Policy.
Import-Certificate -FilePath <CRT file path> -CertStoreLocation Cert:\LocalMachine\Root
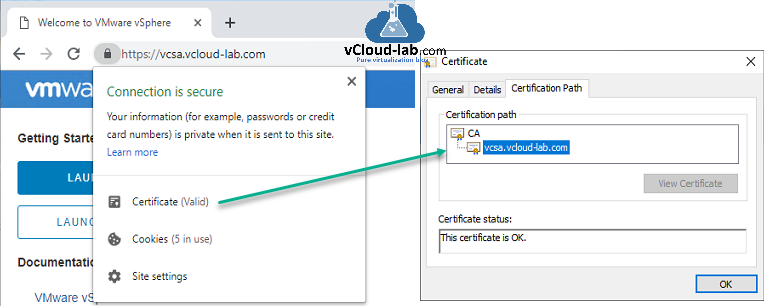
This onetime step is completed, close and reopen vCenter url in browser, this time connection will be show secure with Certificate (valid), and on the cert path it shows proper chain with hierarchy path.
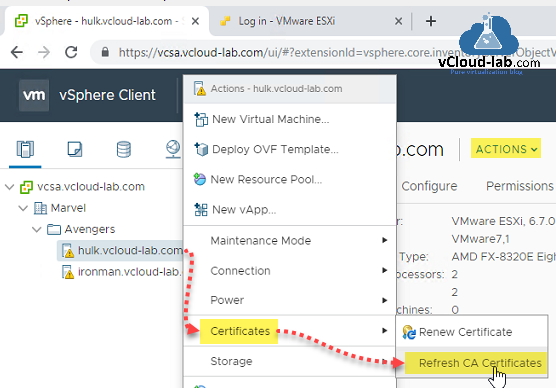
Adding esxi host to vCenter virtual datacenter has its own benefit, the very first in effect is, when you add ESXi host to vCenter, Esxi self signed certificate will be automatically replaced by VMCA signed certificate on ESXi host. In case if you have upgraded vCenter from lower version and after upgrade somehow esxi certificate is not refreshed, you can do it by Right clicking from virtual datacenter on ESXi server and then on context menu actions select Certificates and click Refresh CA Certificates. If certificate is about to expire, you can renew it using Renew Certificate.
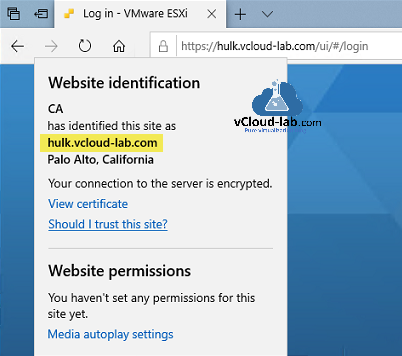
Lunch ESXi ui web access in browser and review the new certificate settings, It is signed by VMware CA now.
Useful Articles
PART 1 : BUILDING AND BUYING GUIDE IDEAS FOR VMWARE LAB
PART 2 : BUILDING AND HARDWARE BUYING GUIDE IDEAS FOR VMWARE LAB
PART 3 : MY VSPHERE LAB CONFIGURATION ON VMWARE WORKSTATION
PART 4 : CONFIGURING VMWARE WORKSTATION NETWORKING IN HOME LAB
PART 5 : CONFIGURING STORAGE IN VMWare WORKSTATION FOR OPTIMAL SPEED
PART 6 : CONFIGURE VMWARE WORKSTATION TO SAVE SSD SPACE AND TIME
PART 7 : CREATING NESTED VMWARE ESXI SERVER VM IN HOMELAB ON VMWARE WORKSTATION
PART 8 : CPU COOLING SOLUTION FOR MY HOME LAB ON VMWARE WORKSTATION