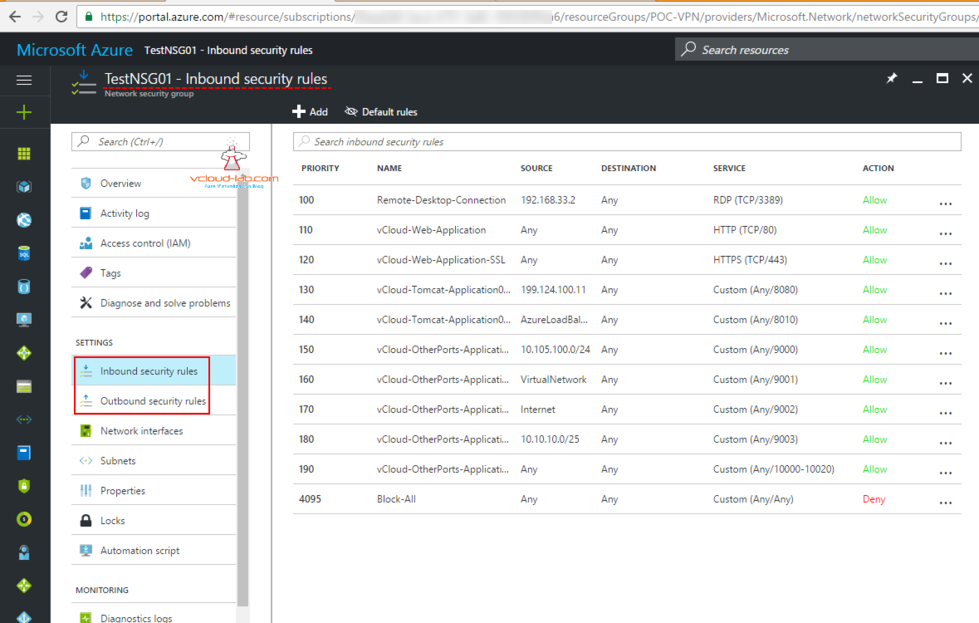
A network security group is a layer of security that acts as a virtual firewall for controlling traffic in and out of virtual machines (via network interfaces) and subnets. It contains a set of security rules that allow or deny inbound and outbound traffic using the following 5-tuple: protocol, source IP address range, source port range, destination IP address range, and destination port range. A network security group can be associated to multiple network interfaces and subnets, but each network interface or subnet can be associated to only one network security group.
POWERSHELL - EXPORT AZURE NSG (NETWORK SECURITY GROUP) RULES TO EXCEL
CREATE NEW NSG (NETWORK SECURITY GROUP - VIRTUAL FIREWALL ACL) ON MICROSOFT AZURE
MICROSOFT AZURE POWERSHELL: CREATING NEW NSG (NETWORK SECURITY GROUP)
MICROSOFT AZURE POWERSHELL: CLONING (COPING) OR IMPORTING EXISTING NSG (NETWORK SECURITY GROUP) FROM EXCEL
Security rules are evaluated in priority-order, starting with the lowest number rule, to determine whether traffic is allowed in or out of the network interfaces or subnets associated with the network security group. A network security group has separate inbound and outbound rules, and each rule can allow or deny traffic. Each network security group has a set of default security rules, which allows all traffic within a virtual network and outbound traffic to the internet. There is also a rule to allow traffic originating from Azure's load balancer probe. All other traffic is automatically denied. These default rules can be overriden by specifying rules with a lower priority number.
In the Classic deployment model, endpoints - with access control lists (ACLs) - were used to control traffic in and out of virtual machines. In the Resource Manager deployment model, traffic can be controlled by using either network security groups or load balancers with inbound NAT rules. While inbound NAT rules are functionally equivalent to endpoints, Azure recommends using network security groups for new deployments where NAT features (like port translation) are not required.
There are no additional charges for creating network security groups in Microsoft Azure.
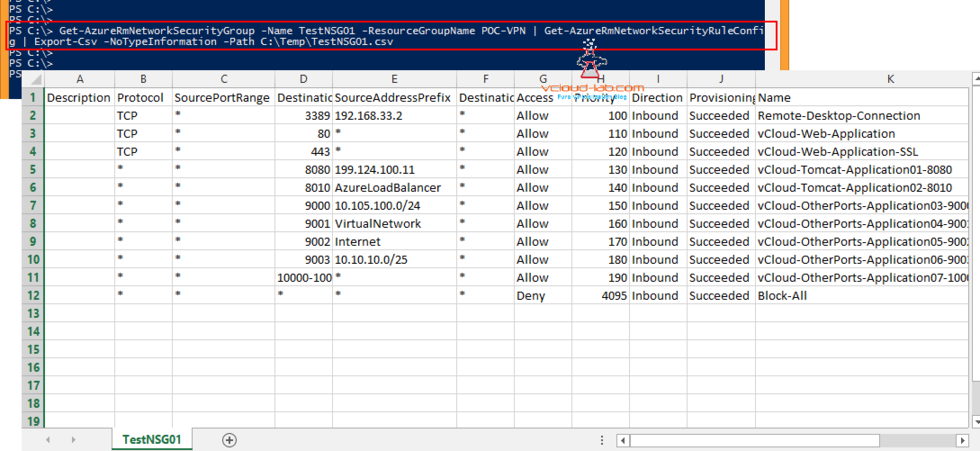
Export the NSG rules to excel is very easy with below Azure Powershell command. Mention the NSG Name and respective Resource Group Name and in the last Export-Csv Path name. (Make sure you have installed Microsoft Azure PowerShell module SDK and logged on Azure using Login-AzureRmAccount). For Inbound and Outbound rules script is same.
Get-AzureRmNetworkSecurityGroup -Name TestNSG01 -ResourceGroupName POC-VPN | Get-AzureRmNetworkSecurityRuleConfig | Select * | Export-Csv -NoTypeInformation -Path C:\Temp\TestNSG01.csv
I can use this exported CSV data to create another NSG (Network Security Group) with all the Rules as it is. Another benefit is csv file can be modified to add or remove Firewall rules.
Useful Links
INSTALLING MICROSOFT AZURE POWERSHELL
PART 9: CREATING AND MANAGING VIRTUAL MACHINE (VM) USING MICROSOFT AZURE RESOURCE MANAGER PORTAL