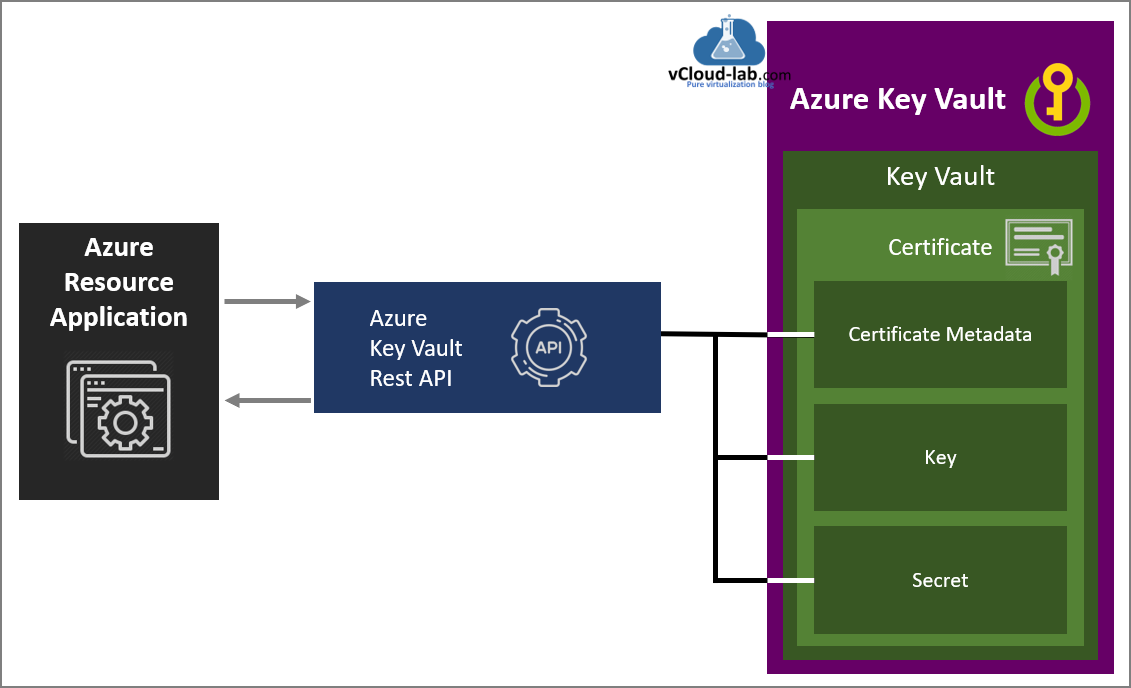
I had one requirement to create a SSL certificates on Azure Key Vault, I have Key Vault already deployed with earlier written articles Create key vault and secrets with access policies in Microsoft Azure. I just wanted to create new SSL certificate in it so using managed Identity In the the future my requirement is to access Azure Key Vault Rest API to connect Key vault and access Certificate Metadata, Keys and Secrets programatically Use a Azure VM system assigned managed identity to access Azure Key Vault.
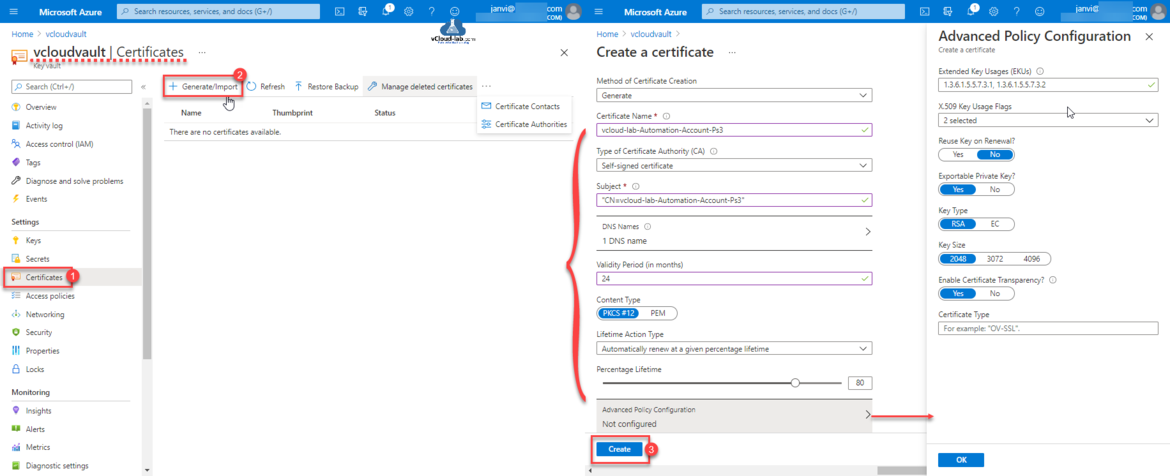
Here in the example on how to use Azure portal to create/generate a certificate on Key Vault, I have selected Key Vault on the portal. Next from navigation pane select certificates and click Generate/Import, Next In the Method of Certificate Creation there are 2 option Generate and Import. Certificate names can only contain alphanumeric characters and dashes.
There are three Type of Certificate Authority (CA) can be used, In this example I will be generating Self-signed certificate (Other options are certificate issued by an integrated CA, ntegrated CAs are managed by key vault, which include: DigiCert,GlobalSign and Certificate issued by a non-integrated CA), Subject Name is The X.500 distinguished name. Subject Alternative Names (SANs) can be specified in the DNS names, you can specify multiple DNS names. Provide Validity Period in months, I want certificate content type in PKCS #12 type. All other options I have kept default. In the Advanced Policy Configuration You can choose different advanced options, the most commonly used item by me is Extended key Usage (EKUs) setting. Click Create.
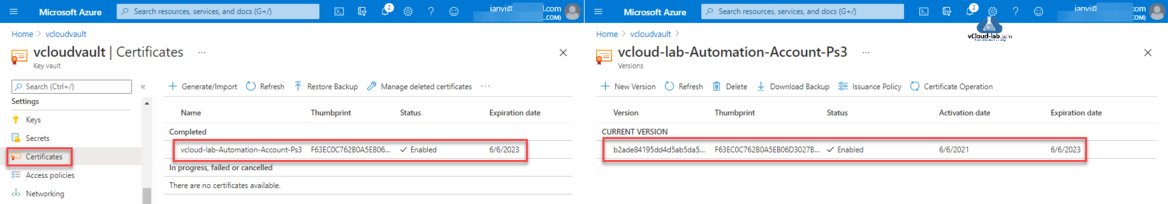
Once you press Create button, it take a few seconds to generate it, while creating certificate it shows disabled under In progress, failed or cancelled, once the process is fully completed the status will be enabled and moved it to completed section. When you click on the certificate you see Versions, You can create a multiple new versions. Click on any of the version.
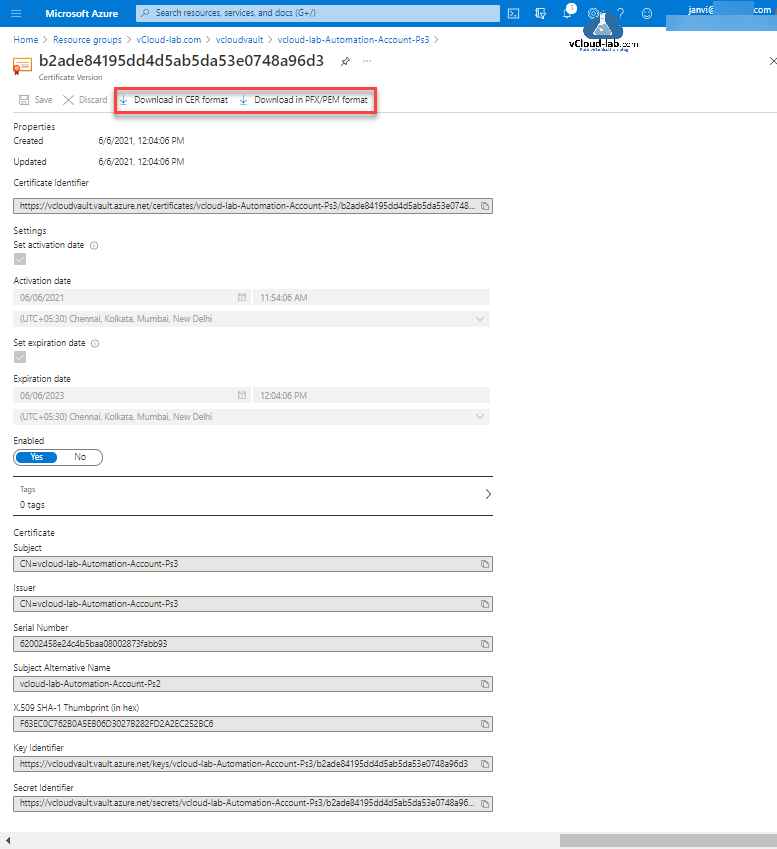
You can view certificate extended properties of that version, useful information can be seen and it is downloaded easily in the CER or PFX/PEM format.
Export certificates from Azure Key Vault using PowerShell
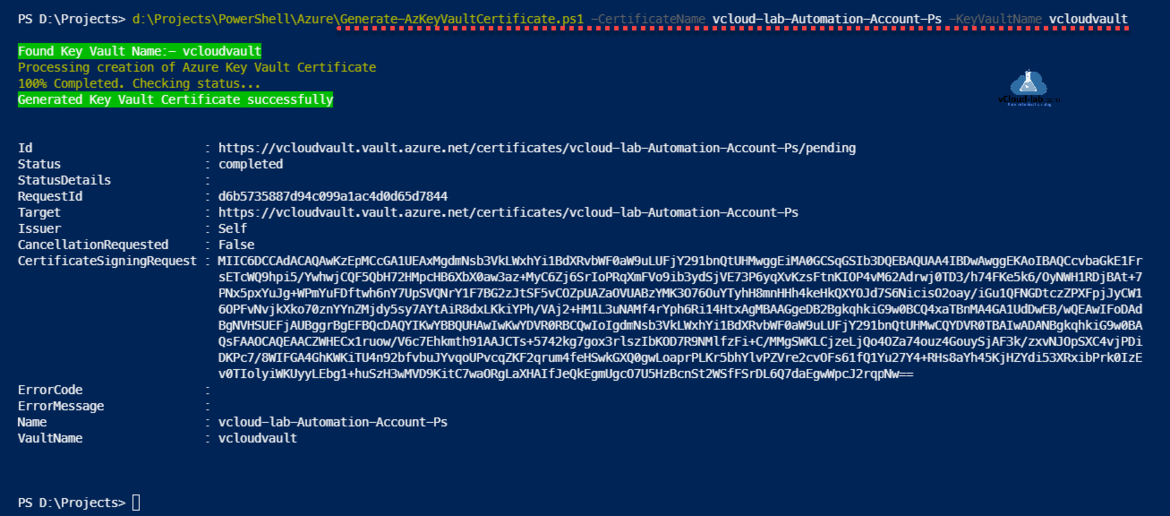
Here instead of manually creating Key Vault certificate on Azure Portal, I wanted the way to create it using Powershell cmdlets for one of my orchestration project. To use this script Key Vault need to be created before hand as shown in blog Working With Azure Key Vault Using Azure PowerShell and AzureCLI, To run below PowerShell script mention CertificateName and KeyVaultName as a parameter. This script if certificate name is not found it creates/generates it or add new version to existing certificate.
.\Generate-AzKeyVaultCertificate.ps1 -CertificateName <Certificate Name> -KeyVaultName <Key Vault Name>
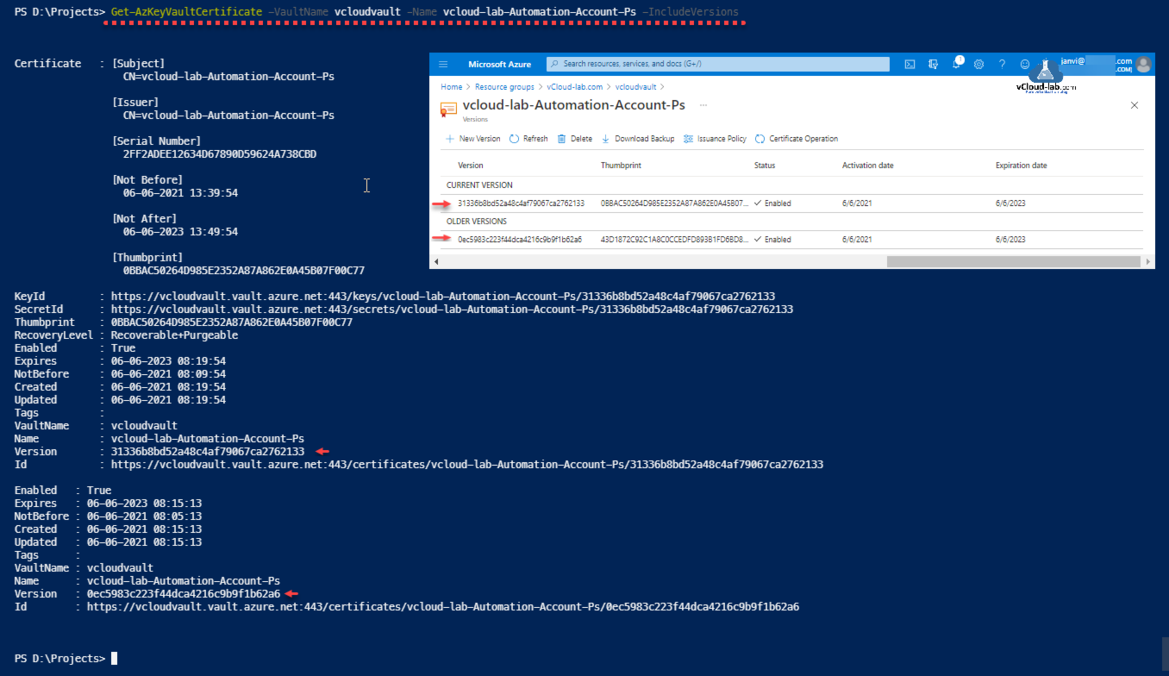
I can verify and check the information of newly generated certificate with below command.
Get-AzKeyVaultCertificate -VaultName <Key Vault Name> -Name <Certificate Name> -IncludeVersions
Here is the Azure PowerShell script.
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 |
[CmdletBinding(
SupportsShouldProcess=$True,
ConfirmImpact='Medium',
HelpURI='http://vcloud-lab.com'
)]
<#
.SYNOPSIS
Generate new Self Singed certificate in Azure Key Vault
.DESCRIPTION
This Script generates new Self Singed SSL certificate in Azure Key Vault, it can create new certificate or update create new version in existing key vault certificate.
.PARAMETER CertificateName
Specify Certificate Name for either new or existing Key vault certificate.
.PARAMETER KeyVaultName
Specify under which key vault you want to generate or update certificate.
.INPUTS
None. Generate or update version of certificate on Key Vault.
.OUTPUTS
Shows information Key Vault Certificate status. You can pipe information to Export-CSV.
.EXAMPLE
PS> .\Generate AzKeyVaultCertificate.ps1 -CertificateName vcloud-lab-Automation-Account-Ps2 -KeyVaultName vcloudvault
Found Key Vault Name:- vcloudvault
Processing creation of Azure Key Vault Certificate
100% Completed. Checking status
Generated Key Vault Certificate successfully
Id : https://vcloudvault.vault.azure.net/certificates/vcloud-lab-Automation-Account-Ps2/pending
Status : completed
StatusDetails :
RequestId : 614c70bba71949c88673253402b8cb80
Target : https://vcloudvault.vault.azure.net/certificates/vcloud-lab-Automation-Account-Ps2
Issuer : Self
CancellationRequested : False
CertificateSigningRequest : MIIC6jCCAdICAQAwLDEqMCgGA1UEAxMhdmNsb3VkLWxhYi1BdXRvbWF0aW9uLUFjY291bnQtUHMyMIIfUjANBgkqhkiG9w0BAQEFAAO
CAQ8AMIIBCgKCAQEArXrw896z/7nwBjNsg2+qEk01S2BcV0ju4Fc1usKBgXAk6jO6pzQru5NNT0Lpdvvx6/y+14Tg01ElHwRHYDbKLD
br+ZjglukebAhSt0zn12bf6UrSGmd2e1BC0F0mo7ZNdwLkNaqAY3/y48YIqAltu6sBQV+lZthAS5vrB0cwNpukG/Y3+MkRuEc909RfF
R6IF88Cd5aHvS8i126BbQSYRhFQTr5z+btQx3BtJKivVRzw+M4CxbmHWkpOstUK4JRUfYhAOylwL2e6JFJiHCQNg0dVsb3Mlkp0cgY3
bHoPBa56754agQzWOV3q238CbmbkAw1HmHcjCT+jraHbEdj1pQIDAQABoHkwdwYJKoZIhvcNAQkOMWowaDAOBgNVHQ8BAf8EBAMCBaA
wHQYDVR0lBBYwFAYIKwYBBQUfgwEGCCsGAQUFBwMCMCwGA1UdEQQlMCOCIXZjbG91ZC1sYWItQXV0b21hdGlvbi1BY2NvdW50LVBzMj
AJBgNVHRMEAjAAMA0GCSqGSIb3DQEBCwUAA4IBAQA2Doge8GLk26h2C8QyaBGBfrEsmf3f4BdX8MTfAAWlprnZYNTfjp4S2JFlthyAZ
afjUKyugaz5zX04mwxRS2XhizXafJGLXploGlYSC/s7YCbGlNirM/5k8AfASP4uLfN23/%^DcqHBt34QOcf7IIIyo1TLfCExhy4c9j0
DLS5oVd0wjKZhFasneW0gf/D-|!an8gZ2KlTHiT75LydDSbkKK+Aufzy8Kn2KBVrJ4PQ2UaUBekMe4MLbxkBzL0W7WUNupwZDlOGYQs
ErrorMessage :
Name : vcloud-lab-Automation-Account-Ps2
VaultName : vcloudvault
.EXAMPLE
PS> .\Generate AzKeyVaultCertificate.ps1 vcloud-lab-Automation-Account-Ps2 vcloudvault
This is another way to execute command .\Generate AzKeyVaultCertificate.ps1 -CertificateName vcloud-lab-Automation-Account-Ps2 -KeyVaultName vcloudvault
.LINK
Online version: http://vcloud-lab.com
.LINK
Get-AzVMBackupInformation.ps1
http://vcloud-lab.com/entries/microsoft-azure/get-azure-virtual-machine-backup-reports-using-powershell
#>
Param
(
[parameter(Position=0)]
[String]$CertificateName = 'vcloud-lab-Automation-Account-Ps',
[parameter(Position=1, ValueFromPipeline=$True, ValueFromPipelineByPropertyName=$True)]
[alias('KeyVault')]
[String]$KeyVaultName = 'vcloudvault'
) #Param
Begin {
#Get existing Azure Key Vault information
$azKeyVault = Get-AzKeyVault -Name $keyVaultName -ErrorAction SilentlyContinue
if ($null -eq $azKeyVault)
{
Write-Host "Didn't find Key Vault with name Azure:- $keyVaultName" -BackgroundColor DarkRed
break
}
else
{
Write-Host "Found Key Vault Name:- $keyVaultName" -BackgroundColor DarkGreen
}
} #Begin
Process {
#Generate new Azure Key Vault Certificate
Write-Host "Processing creation of Azure Key Vault Certificate" -ForegroundColor Yellow
$certSubjectName = 'cn=' + $CertificateName
$azKeyVaultCertPolicy = New-AzKeyVaultCertificatePolicy -SecretContentType "application/x-pkcs12" -SubjectName $certSubjectName -IssuerName Self -ValidityInMonths 24 -ReuseKeyOnRenewal -DnsName $certificateName
$azKeyVaultCertStatus = Add-AzKeyVaultCertificate -VaultName $keyVaultName -Name $CertificateName -CertificatePolicy $azKeyVaultCertPolicy
#Wait for certificate to generate
$counter = 1
While ($azKeyVaultCertStatus.Status -eq 'inProgress') {
Start-Sleep -Milliseconds 50
Write-Host "`r$counter% creation in progress" -NoNewline -ForegroundColor Yellow
$azKeyVaultCertStatus = Get-AzKeyVaultCertificateOperation -VaultName $keyVaultName -Name $CertificateName
$counter++
}
Write-Host "`r100% Completed. Checking status... " -ForegroundColor Yellow
if ($azKeyVaultCertStatus.Status -ne 'completed') {
Write-Host $($azKeyVaultCertStatus.StatusDetails) -ForegroundColor Magenta
}
else {
Write-Host "Generated Key Vault Certificate successfully" -BackgroundColor DarkGreen
Write-Output $azKeyVaultCertStatus
}
} #Process
End {} #end
|
Download this script here or it is also available on github.com.
If you are AzureCLI commands fan, You can use below command to create certificate and view the information. You can this article Working With Azure Key Vault Using Azure PowerShell and AzureCLI to create Key Vault.
az keyvault certificate create --vault-name "<keyvault-name>" --name "<CertificateName>" --policy "$(az keyvault certificate get-default-policy)"
az keyvault certificate show --name "<CertificateName>" --vault-name "<your-unique-keyvault-name>"
Useful Commands
Create key vault and secrets with access policies in Microsoft Azure
Working With Azure Key Vault Using Azure PowerShell and AzureCLI
Use Key Vault secret identifier url to get the secret value using Powershell
Use a Azure VM system assigned managed identity to access Azure Key Vault
Create an Azure App registrations in Azure Active Directory using PowerShell & AzureCLI
Get started and configure with certificate-based authentication in Azure
Create a Virtual machine on Microsoft Azure
PowerShell List All Azure Resverations
Powershell get the list of Azure Reservations Virtual Machines instances
Get the list Azure Reservation Catalog with PowerShell and AzureCLI